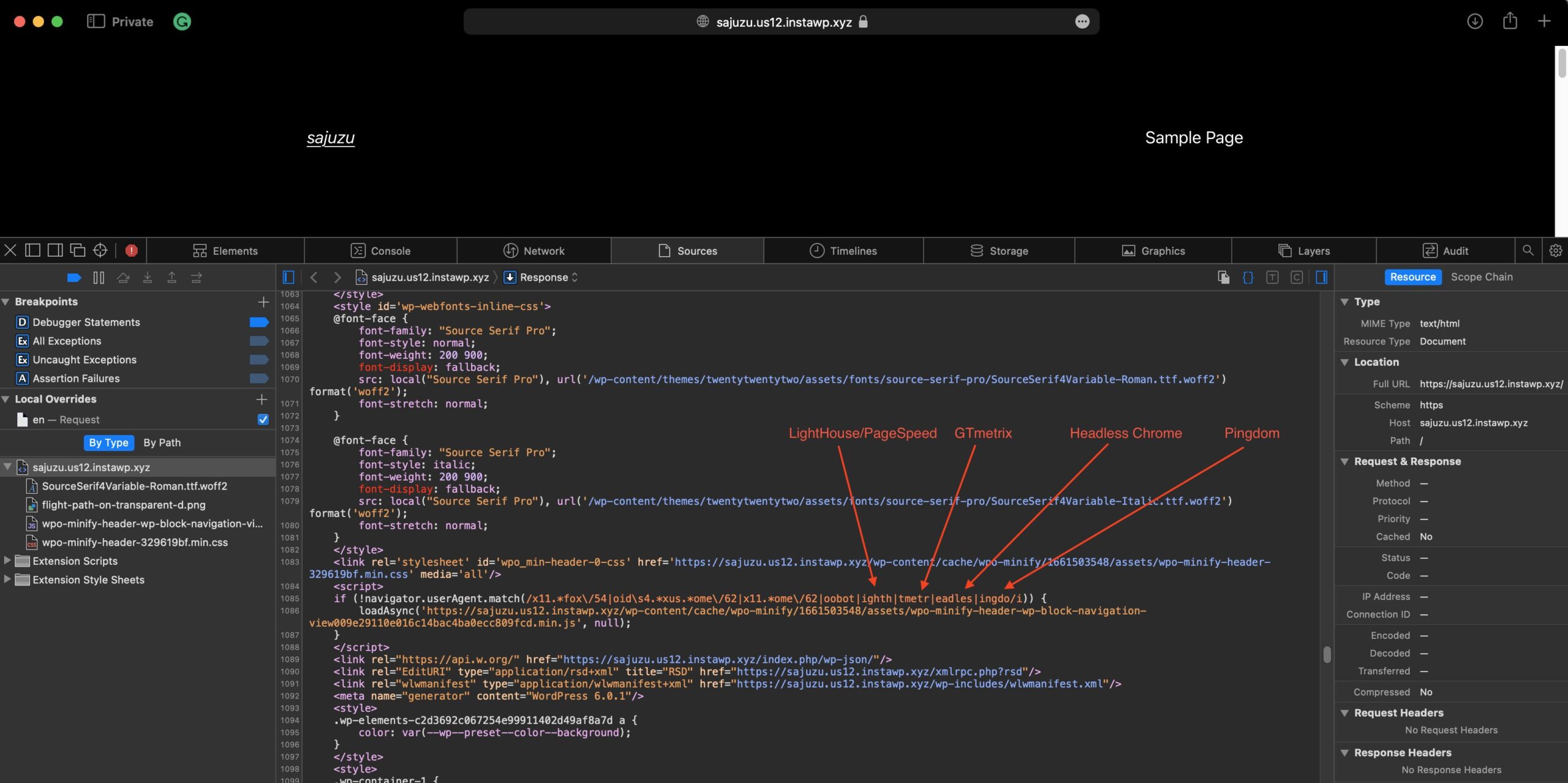
Gijo Varghese, a developer who calls himself a “web performance enthusiast,” shocked WordPress users around the world over the weekend when he tweeted a screenshot of how WP-Optimize is allegedly preventing select JavaScript files from loading when users test their sites through popular performance testing tools.
“When a site is loaded, the JavaScript files are loaded only when the user-agent/browser is not Lighthouse/GTmetrix/Headless Chrome/Pingdom,” Varghese said. “No JS = high scores. But for real users, these JS files are loaded!”
Varghese confirmed that he was testing the free version of WP-Optimize, which is used on more than a million WordPress sites. UpdraftPlus acquired WP-Optimize in 2016 and claims that the tool “has everything you need to keep your website fast and thoroughly optimized.” A commercial version is also promoted through the free plugin that is hosted on WordPress.org.
“Tell me, UpdraftPlus, how I’m supposed to continue trusting your company with my clients’ backups when you use these deceptive and fraudulent practices?” one customer Adam Lowe said in response to Varghese’s discovery of the plugin not loading JS for performance tools.
“Wow, all I can say is what an utter disappointment,” WordPress agency owner and developer Brian Jackson said.
This type of alleged deception is eerily similar to a scam reported by someone who contracted a performance freelancer on Upwork who artificially manipulated Google Pagespeed results. Others participating in the discussion on Twitter compared it to the Volkswagon emissions scandal where the carmaker was found to activate its emissions controls only during laboratory testing in order to meet the EPA’s requirements after a violation. The vehicles on the road emitted up to 40 times more nitrogen oxides while driving, as compared to how they performed in the rigged laboratory tests.
Varghese and several other participants in the conversation concluded that this is why site owners should focus on what real world users are experiencing, instead of performance tool test scores.
Even when focusing on real user experiences, site owners often rely on the tests to diagnose issues and see how a site’s performance can be improved. They don’t expect that a plugin will be hiding JS files from performance tools. Tricking the tests has eroded WP-Optimize’s credibility.
“Wow. If true, this is as short sighted as it is inexcusable,” UpdraftPlus customer Johnathon William said. “And it makes me wonder if I can trust their other product, UpdraftPlus, which I use to backup several client sites.”
I contacted UpdraftPlus and lead developer David Anderson said the company was not aware of the issue with the code but related some of the backstory. UpdraftPlus was briefly in talks with the author of the Fast Velocity Minify plugin about the possibility of combining forces, in which he would maintain the minification module within WP-Optimize and gain more users. Ultimately they could not come to an agreement, but during that time WP-Optimize’s developers forked and adapted Fast Velocity Minify under the GPL. The developers who worked on that adaption are no longer with the company.
“In the commit to our own source repository, 2.5 years ago (Jan 2020), the commit was labelled ‘Resolve ‘Add CSS and JS Minification GPL code from ‘Fast Velocity Minify’ – Part 6′,” Anderson said. “Part of a series of initial merges of code that was re-factored to be cleaner and use our coding style preferences (but not change any functionality). So the apparent intention of the merge of those lines was to bring over refactored code without at that stage making any changes.
“According to the commit history (i.e. the ‘git blame’ function) no changes have been made to that code since, i.e. it is as-imported. (The history for WP Optimize is public in WordPress SVN too).”
After a cursory examination of the code, Anderson concluded that his team may need to reexamine it, as they were not aware of what was added two years ago.
“As I try to trace that function through the code within the plugins, the intention on the face of it appears to be that if the website visitor is a ‘bot,’ then code that is pointless for bots won’t be carried out,” he said.
“However having said that, 1) the bot names look to be heavily obfuscated/redacted, which is strange (why?), and 2) there are plenty of more obvious bots that aren’t listed there, such as the Googlebot itself. If that function was being put before me for review today, I’d certainly question why that is so. I can’t mind-read myself back 32 months ago, but, I remember it as being a long series of large patches, so it wasn’t being closely analysed on a line-by-line basis. We knew that we had identified FVM as a good plugin and our main focus was on adapting it to our structure and style, and those were the things I personally was looking at as the final reviewer.”
In summary, UpdraftPlus’ development team was not aware of this code until the Twitter thread was published over the weekend.
“I’m certainly glad to have it brought to our intention,” Anderson said. “The associated code comment on a related fragment in its original source that it’s intended to prevent unnecessary requests for bots, but on a closer examination than that line got at the time, that’s something we’ll want to look at, as it does look questionable/strange, and we’ll be doing that by assigning it to a team member who’s our expert in JavaScript optimizations.”
Anderson also said that if the JavaScript optimization experts cannot find any legitimate purpose for the code, “it will certainly be removed,” with a clear and unambiguous disclosure for the reasoning behind it.
In the meantime, UpdraftPlus has published a notice in the plugin’s support forum to inform users that the code is currently under investigation.
“To be clear and set users’ minds at rest: the code in question is not dangerous, a virus, an infection, useful to hackers, or anything of that kind,” Anderson said. “The allegation is that its only purpose in existing is effectively to cheat on speed tests. Such code, if so, does not belong in WP Optimize and we will remove it with a new release. Our products’ integrity, and our customers’ trust, are essential for us (and deliberately putting things in open source code that compromises that is, frankly, a stupid thing to do).”
Discover more from The Kashmir Monitor
Subscribe to get the latest posts to your email.